What is Penetration Testing?
Penetration testing, also known as pen testing, is a type of ethical hacking that simulates a real-world attack on a computer system, network, or web application to identify vulnerabilities that could be exploited by malicious actors. Pentesting is a key aspect of good cyber security.
The main goal of a penetration test is to assess the security of a system or application by attempting to exploit its vulnerabilities in a controlled, ethical manner.
The results of a pen test can be used to prioritise security improvements and mitigate potential risks. There is a wide range of penetration testing tools available for ethical hackers to utilise, and these are often the same tools relied upon by adversaries.
Why Is Penetration Testing So Important?
According to the 2023 Open Source Security and Risk Analysis (OSSRA) report, Synopsys researchers reported that at least one open source vulnerability was found in 84% of code bases. Since most software applications rely on open source code, having effective penetration testing in place is vital.
There are several more reasons why penetration testing is important for organisations:
-
Identify vulnerabilities: Penetration testing helps identify vulnerabilities in your systems before attackers can exploit them. By simulating real-world attacks, penetration testing can reveal weaknesses that might go unnoticed otherwise.
-
Prevent data breaches: By identifying security flaws, penetration testing helps prevent data breaches that can lead to significant financial and reputational damage.
-
Meet compliance requirements: Many industries and regulatory bodies require regular penetration testing to comply with industry regulations and standards.
-
Improve security posture: Penetration testing provides a clear understanding of an organisation's current security posture and helps prioritise security investments based on risk.
-
Test incident response: Penetration testing can test an organisation's incident response capabilities and identify areas for improvement.
Overall, penetration testing is an essential component of any comprehensive cybersecurity strategy, helping organisations identify and address known vulnerabilities before they are exploited by attackers.

What Should A Penetration Test Tell You?
As a penetration testing provider, we believe that a comprehensive test should give you a clear picture of the security posture of your organisation.
A penetration test should identify the vulnerabilities and weaknesses in your network and system’s security, highlight potential attack paths and vectors, and provide recommendations for remediation. It should also give you an understanding of your organisation's ability to detect and respond to an attack.
A good penetration test report should be actionable and provide guidance on how to prioritise and address identified vulnerabilities. Ultimately, the goal of a penetration test is to improve your organisation's security posture by addressing weaknesses before a bad actor can exploit them.
What Sort of System Should Be Tested?
All types of computer systems, networks, applications, and devices that are used to store, process, or transmit sensitive data should be tested. This includes web applications, mobile applications, wireless networks, cloud-based systems, and IoT devices.
The scope of the penetration test should be determined by the organisation's risk assessment and compliance requirements. It's important to test all systems and applications that have access to valuable data to ensure that they are secure and protected against potential attacks.
Why Does Your Organisation Need A Penetration Test?
The cost of a data breach is a growing concern for organisations worldwide. According to Statista's latest research, in 2022, the global average cost of a data breach has skyrocketed to a staggering $4.35 million. Additionally, their forecast indicates that global cybercrime costs will continue to rise at a significant rate of 23% annually over the next five years.
By 2027, these costs are projected to reach a whopping $23.84 trillion per year, making the need for robust cybersecurity measures more critical than ever before.
Penetration testing is an essential security practice that all organisations should consider implementing. With cyber attacks becoming increasingly sophisticated and frequent, it is essential to test your organisation's defences and identify any vulnerabilities before they are exploited by attackers.
What Are the Benefits of Penetration Testing?
the benefits of penetration testing can be summarised as follows:
-
Identify vulnerabilities: Penetration testing can uncover security weaknesses that could be exploited by attackers. By identifying vulnerabilities, organisations can take action to mitigate the risk of an attack and gain critical insight into the organisation's attack surface.
-
Improve security posture: Penetration testing can help organisations improve their overall security posture by identifying gaps in security controls and processes. This can help organisations prioritise security investments and focus on areas that need improvement.
-
Meet compliance requirements: Many regulations and standards require regular penetration testing, such as PCI DSS, HIPAA, and ISO 27001. Penetration testing can help organisations meet these requirements and avoid potential fines or legal issues.
-
Test incident response capabilities: Penetration testing can also test an organisation's incident response capabilities. By simulating an attack, organisations can test their ability to detect, respond to, and recover from a security incident.
-
Gain stakeholder confidence: Penetration testing can demonstrate to stakeholders, including customers, partners, and investors, that an organisation takes security seriously. This can help build trust and confidence in the organisation's ability to protect sensitive data and assets.
Types of Penetration Testing
Each type of penetration testing serves a specific purpose in identifying vulnerabilities and weaknesses in an organisation's security posture. It's important for organisations to perform a combination of these tests to gain a comprehensive understanding of their security risks and to prioritise remediation efforts.
Here are some of the different types of penetration and the objectives associated with each:
Web application pen testing
Penetration testers focus on identifying vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and broken authentication. Penetration testers aim here is to identify weaknesses that attackers could exploit to gain unauthorised access to sensitive information or take control of the application.
Mobile application pen testing
Mobile application pen testing involves testing the security of mobile applications on various platforms, such as iOS and Android. The testing includes identifying security flaws that could be exploited by attackers to gain access to sensitive information or control the mobile application.
Cloud environment pen testing
This type of testing is focused on identifying vulnerabilities in cloud-based environments, such as Amazon Web Services (AWS) and Microsoft Azure. The testing includes identifying weaknesses in cloud infrastructure, such as misconfigured settings and unpatched systems, that could be exploited by attackers to gain access to sensitive information. External infrastructure penetration tests This type of testing involves testing the security of external-facing systems, such as firewalls, routers, and web servers. The goal is to identify vulnerabilities that could be exploited by attackers to gain access to the organisation's network and systems.
Internal infrastructure penetration tests
Internal infrastructure pen testing involves testing the security of internal systems, such as employee workstations and servers. The internal test includes identifying vulnerabilities that could be exploited by attackers who have already gained access to the organisation's network.
Physical penetration tests
Physical pen testing involves gaining access to an organisation's physical facilities, such as buildings and critical assets. Penetration testers attempt to gain physical access to sensitive areas by bypassing physical security controls, such as keycard readers and security guards.
Social engineering penetration tests
Social engineering pen testing involves testing the effectiveness of an organisation's security awareness training and policies. Security experts use social engineering tactics to attempt to trick employees into divulging further information or performing actions that could compromise the organisation's security.
Open-source intelligence
Open-source intelligence involves gathering publicly available information about an organisation, such as its employees, systems, and vendors. The information can be used to identify potential vulnerabilities and weaknesses that could be exploited by attackers.
Penetration Testing Stages
Penetration tests typically follow a structured approach consisting of initial engagement, scoping, testing, reporting, and follow-up. The aim of such a test is to determine the potential impact of a vulnerability being exploited by an attacker, as well as the likelihood of such an attack occurring. It's also assumed that there's an internal vulnerability assessment and management process in place.
During the initial engagement phase, it's important to ensure that the external team has the necessary qualifications and skills to conduct testing on your IT infrastructure. If there are any unusual or non-standard systems such as mainframes, bespoke hardware, or uncommon networking protocols, these should be highlighted during the bidding process so that the external team can provide a tailored approach.
Additionally, after conducting the penetration testing, the external team should provide a report that includes a severity rating for any issues discovered. This report will assist in identifying areas that require remediation to improve your overall security posture. Finally, it's essential to follow up with the external team to discuss the report's findings and develop a plan of action to address any identified vulnerabilities.
Here is a breakdown of the different stages of a model penetration test:
Planning and reconnaissance
In this stage, the penetration tester works with the client to identify the scope of the test and gather as much information as possible about the target environment. This includes identifying potential targets, analysing network and system architecture, and gathering any other relevant information.
Scanning
The next stage involves using automated tools to scan the target environment for vulnerabilities. This includes identifying open ports, services, and software versions that may be vulnerable to attack.
Enumeration
Once potential vulnerabilities have been identified, the penetration tester will attempt to gain more information about the target environment. This may include using tools to extract information about user accounts, network resources, and system configurations.
Exploitation
In this stage, the penetration tester attempts to exploit any vulnerabilities that have been identified. This may involve using custom scripts or other tools to gain access to the target system or network.
Post-exploitation
Once access has been gained, the penetration tester will now focus on maintaining access to the target environment in order to gather as much information as possible. This may involve using various techniques to escalate privileges, harvest sensitive data, or pivot to other systems within the target environment.
Reporting
Finally, the penetration tester will provide a detailed report to the client that outlines the vulnerabilities that were identified, the methods used to exploit them, and any recommendations for mitigating these vulnerabilities. The report may also include detailed remediation steps and a summary of the overall risk to the target environment.
What’s the Difference Between Penetration Testing and Vulnerability Assessments?
Vulnerability assessments are typically automated or manual processes that scan a system or application to identify potential security weaknesses, such as outdated software, misconfigurations, or other vulnerabilities. The results of a vulnerability assessment provide a prioritised list of vulnerabilities, along with recommendations for addressing them.
Penetration testing, on the other hand, is a more targeted and comprehensive security assessment. As previously mentioned, It involves attempting to exploit identified vulnerabilities and gain unauthorised access to sensitive data or systems.
The goal of a penetration test is to launch a realistic simulated attack and identify any weaknesses that could be exploited by attackers.
In short, vulnerability assessments are focused on vulnerability identification, while penetration testing goes further by attempting to exploit those vulnerabilities and assess the actual risk to the organisation. Both are important components of a comprehensive security testing program, and both aid organisations in gaining assurance in their information security, but they serve different purposes and should be used in conjunction with each other.
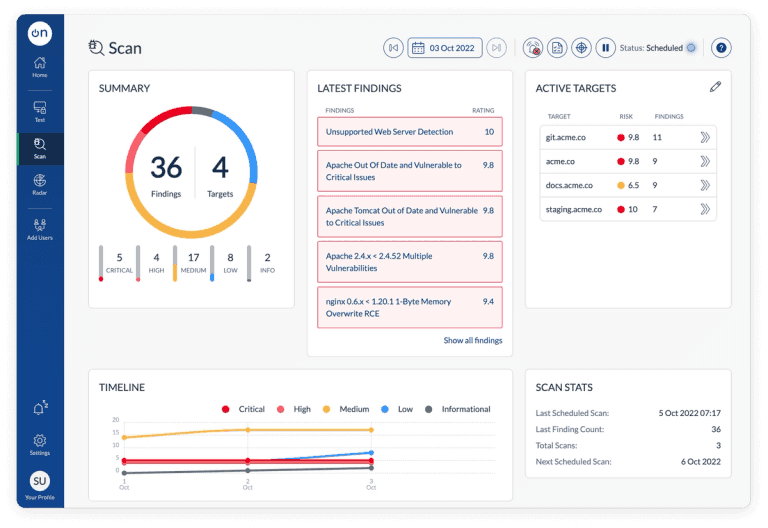
Scan By OnSecurity
Scan by OnSecurity monitors your external estate, finding and reporting vulnerabilities in your Internet-facing infrastructure before the hackers do, so you can take action and prevent breaches.
Reduce risk and have effortless compliance by using our cutting edge technology, and better yet, it's free to get started here!
How Much Does A Pen Test Cost?
The cost of a penetration testing service can vary depending on the scope, duration, and complexity of the project. Generally, factors that can affect the cost of a penetration test include the number of systems to be tested, the depth and breadth of the testing, the type of testing required (e.g., web application, network, mobile), and the level of reporting and follow-up support needed.
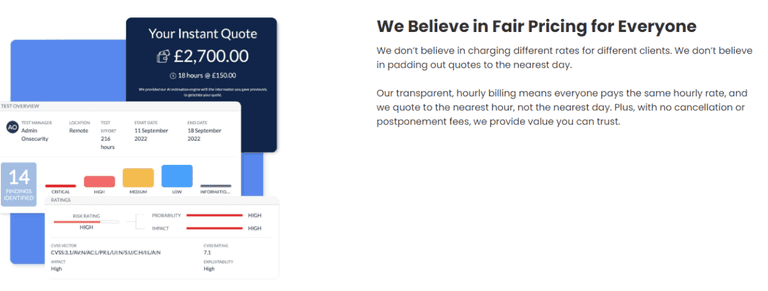
Our transparent, hourly billing means that everybody pays the same rate, and we quote to the nearest hour, not the nearest day.
If you are interested in obtaining a quote for a penetration test, you can get an instant quote here!
OnSecurity - Pentesting At The Speed Of Business.
We believe in simple online booking. We believe in hourly billing and transparent pricing. We believe in real-time reporting. We believe in no cancellation or postponement fees.

More Cost Effective
With our precise hourly billing, and zero reporting charges our clients with multiple pentest requirements save an average of 38% on their annual pentesting bill (versus previous provider).
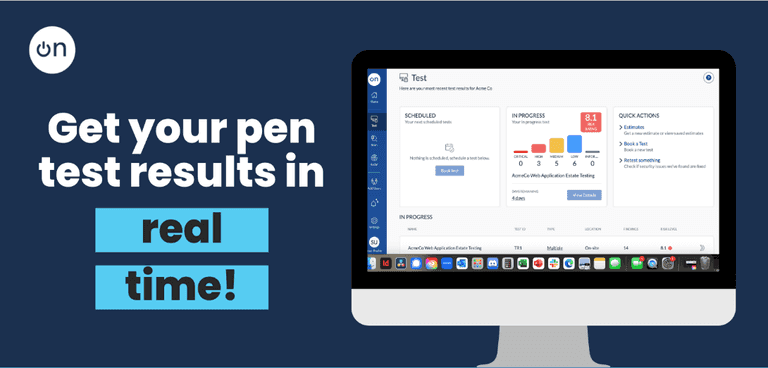
Real-Time Reporting
With our online booking, on-demand scheduling and real-time reporting, our average project turnaround time (initial engagement to comprehensive report completion) is 10 days, versus the industry average of 42 days.
Hourly Billing
We don't charge postponement and cancellation fees. We don't charge for re-testing booked within 7 days of issue identification. These features alone represent an average saving of £1,070 per engagement vs other providers.
CREST APPROVED
OnSecurity is a CREST-approved vendor, and we offer a wide range of industry leading global penetration testing services to our clients. If you are looking to find out how much a penetration test costs, you can get an instant quote now!
Take the next step.
How can OnSecurity help?
As a trusted provider of cybersecurity services, OnSecurity offers best-in-class penetration testing to help identify and address potential vulnerabilities within your organisation's IT infrastructure. Our experienced team utilises industry-leading techniques and tools to thoroughly assess your systems and provide actionable insights to enhance your overall security posture.
For further information, or if you have any specific enquiries around this please contact us or request an instant quote now!

OnSecurity is a CREST-approved vendor, and we offer a wide range of industry leading global penetration testing services to our clients.