Our internal infrastructure penetration testing pinpoints vulnerabilities within your network, simulating real-world attacks to show exactly where you're exposed. Get immediate insights to fix weaknesses, prevent unauthorised access, and protect critical systems before attackers strike.
Internal infrastructure penetration testing
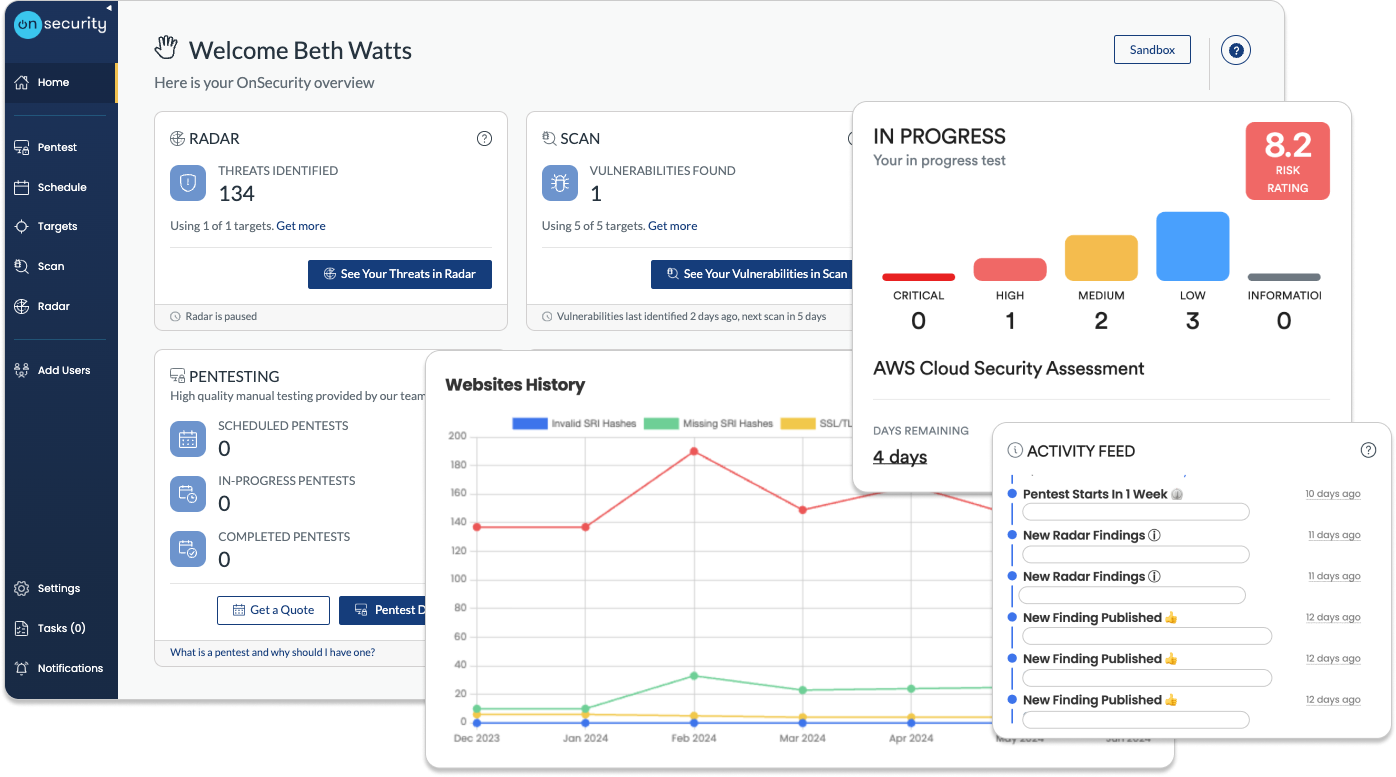
Internal infrastructure penetration testing with OnSecurity
Our internal infrastructure penetration testing goes beyond surface-level assessments, delivering expert-driven insights into your network's weaknesses.
Reveal hidden weaknesses
You'll gain insight into unpatched and insecure systems and services that could leave your network exposed, identify vulnerable areas attackers could exploit to access staff accounts or critical systems and understand how to prevent unauthorised control of workstations or servers.
Strengthen access security
Ensure stronger protection against intercepted or cracked passwords, safeguard your network from brute force attacks on key services like databases and web applications and secure privileged accounts, such as domain administrators, from potential compromise.
Safeguard critical information
Find ways to prevent unauthorised access to sensitive or mission-critical information, block attackers from establishing a foothold in your network and remain undetected and secure internal communications from potential eavesdropping and exploitation.
What is internal infrastructure penetration testing?
Internal infrastructure penetration testing is ethical hacking of the internal Windows (usually) network infrastructure that belongs to an organisation.
An internal penetration test evaluates the security of your internal infrastructure. It simulates scenarios where an attacker has already breached your network, looking for vulnerabilities to exploit. These attackers could be internal (e.g., unhappy employees) or external actors who have gained access through vulnerabilities, malware, or stolen credentials.
Key aspects of internal penetration testing include the ability to target internal networks, hosts, applications, or a combination of these based on specific needs, and the role of testers to identify access points and attempt lateral movement within the environment.
Get an Instant Internal Infrastructure Pentest Quote
Want to know how much an internal infrastructure pentest would cost? Try out our instant quote generator to get started.
Why do you need an internal network infrastructure pentest?
When attackers target an organisation, their goal is to gain access to its internal network, either by breaching the perimeter or through social engineering tactics like phishing. Once inside, they attempt to reach the organisation’s most valuable assets—the "crown jewels"—by moving through the network, compromising accounts and systems along the way.
An internal infrastructure penetration test assesses how well your network is protected from an attacker who has already gained a foothold. It reveals how easily an attacker could navigate through your network, steal data, or take control of critical systems.
The benefit of this test is that it allows ethical hackers to safely uncover vulnerabilities and identify paths to critical assets, giving you the opportunity to fix weaknesses before malicious attackers exploit them. Without penetration testing, you increase your risk of security breaches that can result in financial losses and severe reputational damage.
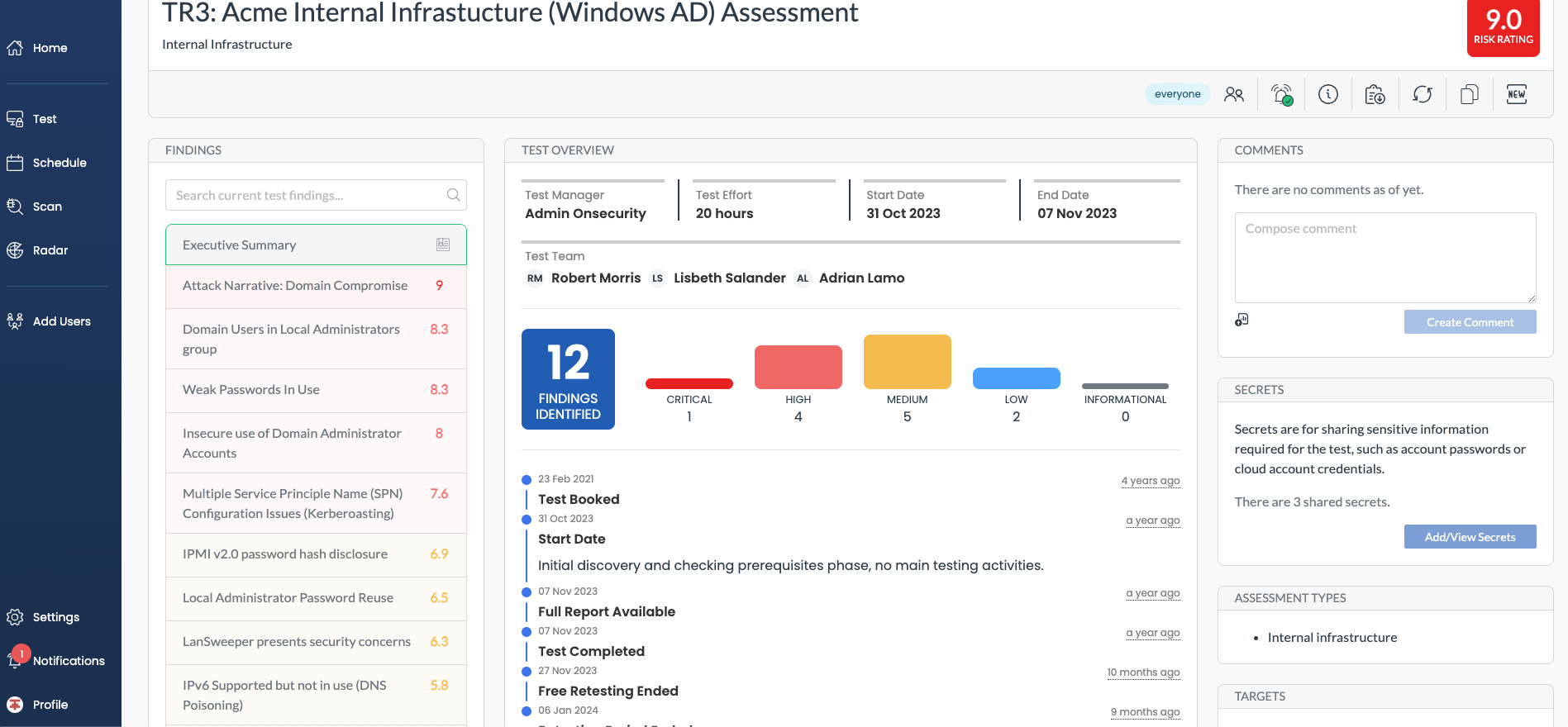

Crest-accredited internal infrastructure pentesting
At OnSecurity, we provide industry-leading penetration testing services, backed by our CREST (Council of Registered Ethical Security Testers) certification. This guarantees that our testing methodologies, procedures, and standards meet the highest levels of excellence. Why choose OnSecurity for your internal infrastructure pentesting?
- CREST-certified: Our services are externally verified, ensuring thorough and reliable testing.
- Expert professionals: Our team consists of CREST-certified testers, skilled in rigorous industry evaluations.
- Hands-on testing: We prioritise manual testing to uncover vulnerabilities that automated tools might overlook.
Trust OnSecurity for thorough, expert-led protection of your internal network.
Internal network security challenges
Securing your internal infrastructure presents unique challenges that require specialised knowledge and proactive measures:
Insider threats
Internal users can inadvertently or maliciously compromise the network.
Complex attack vectors
Cybercriminals may combine multiple vulnerabilities across systems to infiltrate the network.
Evolving threats
Attack techniques constantly evolve, necessitating regular assessments to stay secure.
Quick, high-quality pentests
Discover why our user-friendly platform and AI + human approach make pentesting hassle- free.
Flexible subscription plans
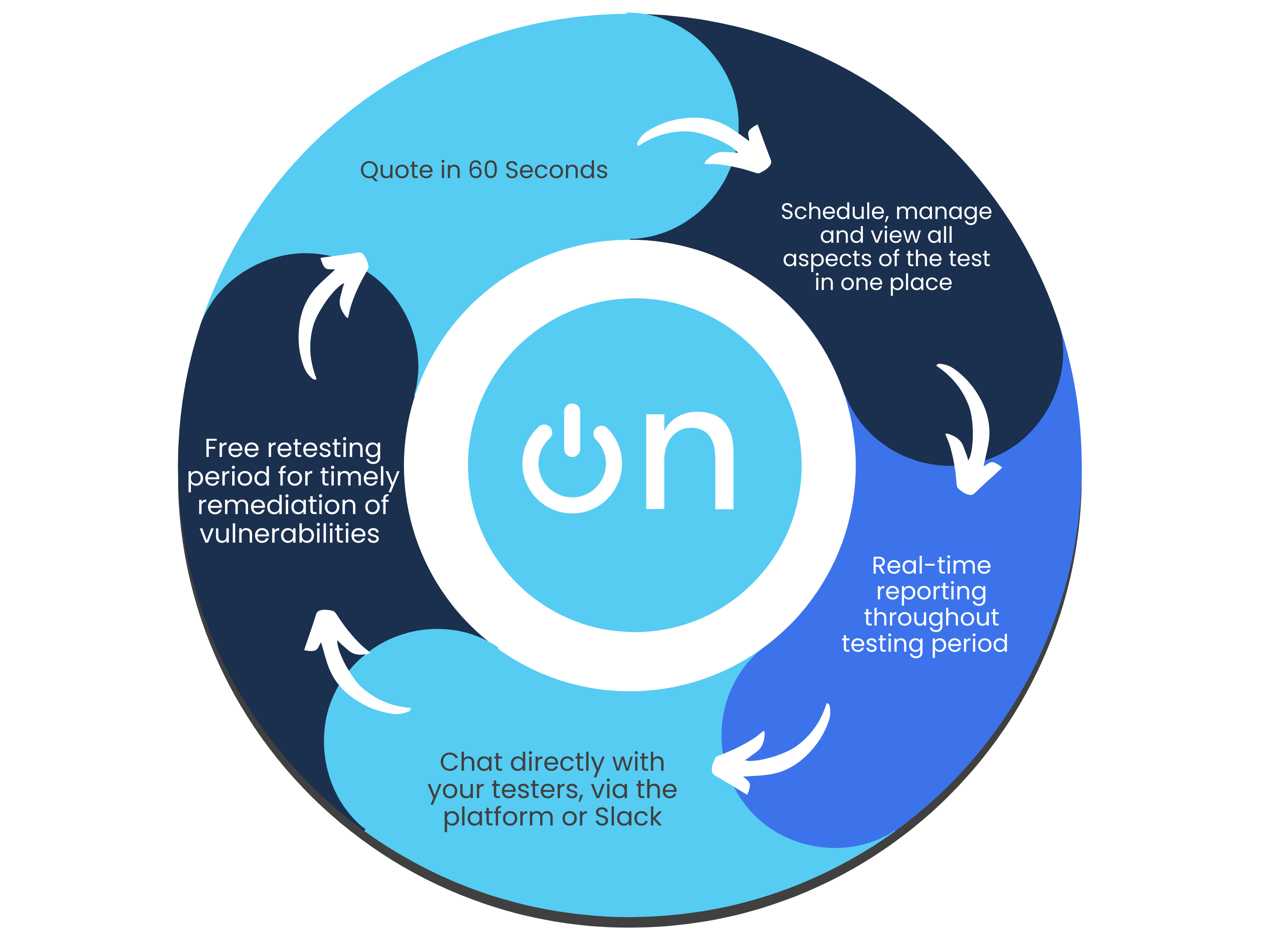
Simplify your testing and monitoring with a single monthly payment, combining regular penetration tests and continuous vulnerability scanning. Get predictable costs while receiving ongoing protection.Instant quote & customised plans
Receive a real-time, personalised cost estimate through our intuitive platform. Tailor your testing needs with configurable options that suit your business goals and security requirements.Effortless platform access
No more long scoping processes. Book tests directly through our platform or get personalised assistance from our sales team. Enjoy streamlined communication and automated workflow notifications for maximum efficiency.Continuous, real-time testing
Stay informed with real-time progress notifications and direct communication with testers via in-platform comments. Benefit from ongoing vulnerability assessments to proactively detect and address risks.Immediate, actionable reports
Access your findings instantly through our platform. Generate detailed reports at any time, offering both technical insights and high-level summaries—without the wait.Free retests for resolved issues
Once you’ve addressed vulnerabilities, we’ll retest them for free within a flexible window, ensuring your systems remain secure at no additional cost.Ongoing protection & threat intelligence
Sign up for continuous monitoring to access automated vulnerability scanning, along with situational awareness through threat intelligence, ensuring your defences stay up to date year-round.
Other types of penetration testing
Find the penetration test to best suit your business and cybersecurity needs.
Frequently Asked Questions
What is the difference between internal infrastructure pen testing and external pen testing?
Internal infrastructure penetration testing focuses on detecting vulnerabilities within an organisation’s internal network, simulating scenarios where an attacker has already gained access. In contrast, external penetration testing targets outward-facing systems, such as web servers and firewalls, to simulate attacks from outside the network perimeter. Internal tests assess risks after a breach, while external tests aim to prevent initial intrusions.
How long does an internal pen test take?
The length of time for each internal pen test can vary. We can provide a tailored estimate for the time needed for your internal penetration test following two straightforward scoping questions. This gives us a chance to evaluate the complexity of the environment and the size and functionality of your target.
How often should you conduct an internal infrastructure pentest?
An internal infrastructure penetration test should typically be conducted at least once a year. However, more frequent testing may be necessary if there are significant changes to the network, such as system upgrades, new applications, or after a security breach. Plus if your organisation has strict regulatory requirements or high-security environments to adhere to, it may benefit from conducting tests more regularly, such as quarterly or biannually, to ensure continuous protection against evolving threats.
When will I receive my pentest report?
Our testers keep you informed with updates during the testing process, delivering notifications directly to your workflow apps as vulnerabilities are uncovered. This ensures you're aware of any issues as they arise, without having to wait for the final report to take action.
Will my internal network be disrupted during the test?
Our experienced professionals conduct penetration tests with precision and care, ensuring no major disruption to your operations. We offer the flexibility to perform tests in UAT, staging, or development environments to further reduce any impact. Throughout the process, we provide continuous updates, enabling you to swiftly address any security concerns as they are identified.
What will we find in an internal infrastructure penetration test?
Our internal penetration test provides valuable insights, including a detailed account of how vulnerabilities were combined to compromise your network, an overview of the main vulnerabilities discovered, information on weak passwords cracked, and details on service misconfigurations. Most importantly, we provide actionable recommendations to fix these issues and prevent real-world attackers from exploiting them.
Is internal infrastructure testing right for your business?
Regular infrastructure penetration testing is a crucial part of any organisation's cybersecurity strategy. We recommend conducting a comprehensive test, covering both internal and external networks, at least once a year. In addition, it's important to perform relevant tests before launching any new systems, following significant changes to internal or external infrastructure, to ensure these assets don’t introduce new vulnerabilities.
Alongside penetration testing, we also advise continuous vulnerability scanning, and threat intelligence. Staying proactive with patch management and remediation is essential. If you have more questions to help select a reputable pen testing service, don’t hesitate to get in touch.
