Your mobile application is a critical business asset that requires robust security across all devices. Comprehensive penetration testing helps identify and address vulnerabilities, ensuring the safety of your iOS and Android applications on various devices. Regular pentests are essential to safeguard customer accounts and sensitive data, keeping your business secure against evolving threats.
Mobile application penetration testing
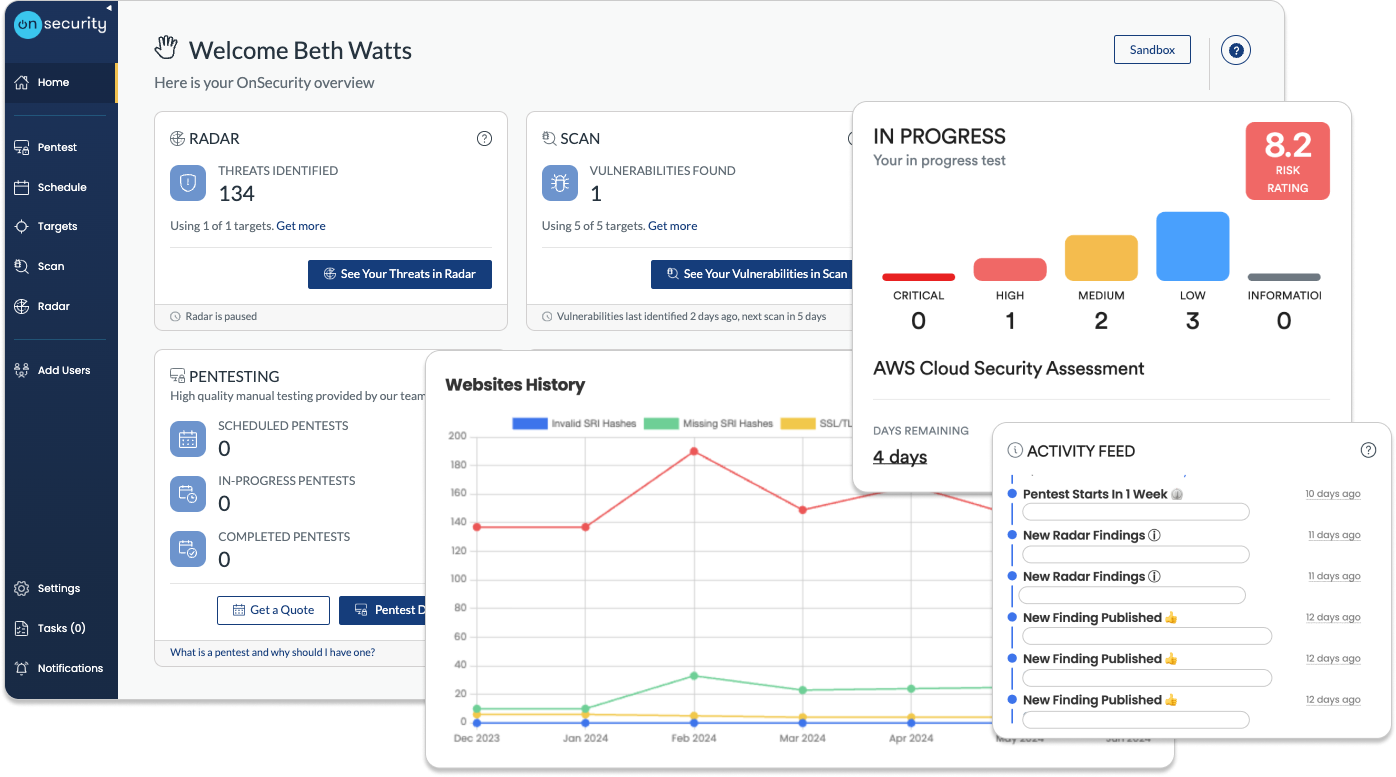
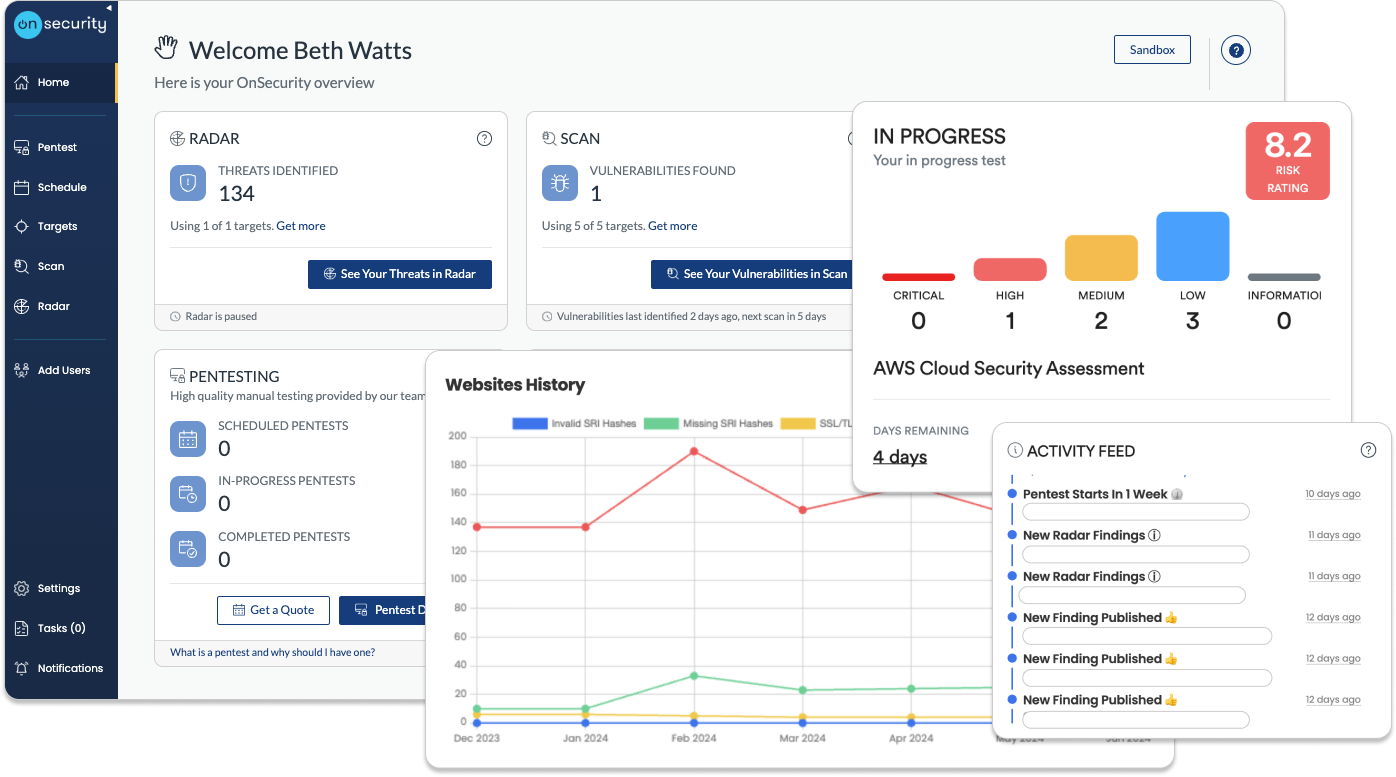
Mobile application penetration testing with OnSecurity
Insecure mobile apps can expose sensitive information to attackers. That’s why proactive security measures, including thorough penetration testing, are crucial. Our team specialises in mobile applications on both iOS and Android.
Identify and understand your vulnerabilities
You'll be able to uncover where your mobile app is most exposed to threats, discover how attackers could exploit these weaknesses and receive clear guidance on how to address these security issues.
Enhance access controls
You'll be able to ensure that only authorised users can access sensitive app features, strengthen user authentication and session management processes and prevent unauthorised access or privilege escalation within the app.
Safeguard sensitive data
Ensure you detect any flaws that could allow data theft or leaks, validate that your data encryption and storage methods are secure and address potential security gaps that could lead to data breaches.
What is mobile application penetration testing?
Mobile application penetration testing is a simulated security assessment designed to uncover vulnerabilities within a business's mobile app. This helps identify potential weaknesses that could be exploited to:
- Unauthorised access to user accounts
- Compromise sensitive app data
- Cause reputational damage
- Harm the app's functionality
Each of these risks can have a substantial impact on the mobile application, its users, and your company. Our CREST-accredited testers use a combination of manual techniques and automated tools during mobile app penetration testing to identify vulnerabilities that real-world attackers might exploit for financial gain.
Mobile application penetration testing can help identify vulnerabilities across areas such as credential usage, supply chain, authentication, input/output validation, communication, privacy, binary protections, configurations, data storage, and cryptography.
Get an Instant Mobile App Pentest Quote
Want to know how much a mobile application pentest would cost? Try out our instant quote generator to get started.
Why do you need a mobile application pentest?
Mobile applications are prime targets for cybercriminals looking to steal data, disrupt services, or damage your brand. With increasing threats, a mobile application pentest is essential. It simulates real-world attacks to uncover and fix vulnerabilities, preventing costly breaches and downtime. Regular pentesting not only protects your business but also shows a commitment to security, boosts customer trust, and ensures compliance with regulations, safeguarding your reputation and bottom line from cyber risks.

Crest-accredited mobile application pentesting
As a CREST-approved provider, we adhere to the highest industry standards, giving you confidence in the security of your applications:
- Our methodologies and processes undergo thorough external evaluation to ensure top-quality testing.
- Our pentesters are CREST-certified, having proven their skills through rigorous assessments.
- We use a "manual-first" approach to identify vulnerabilities that automated tools might overlook.
With OnSecurity, you receive unparalleled expertise and comprehensive protection for your mobile applications, so your security needs are fully met.
Mobile application security challenges
Mobile app security presents critical challenges for businesses, and staying ahead of these threats is essential. Here's what you should be concerned about:
Data breaches
Mobile apps remain a major target for attackers due to the sensitive data they handle. Data breaches can result in substantial fines and reputational harm, threatening both trust and financial stability.
Insecure code practices
Poor coding practices, such as inadequate input validation and improper handling of user data, create vulnerabilities that can be exploited by attackers.
Evolving threat landscape
The rapid evolution of mobile malware, such as mobile bankers, spyware, and crypto-jacking, along with new risks posed by the proliferation of 5G, demands specialised expertise.
Quick, high-quality pentests
Discover why our user-friendly platform and AI + human approach make pentesting hassle- free.
Flexible subscription plans
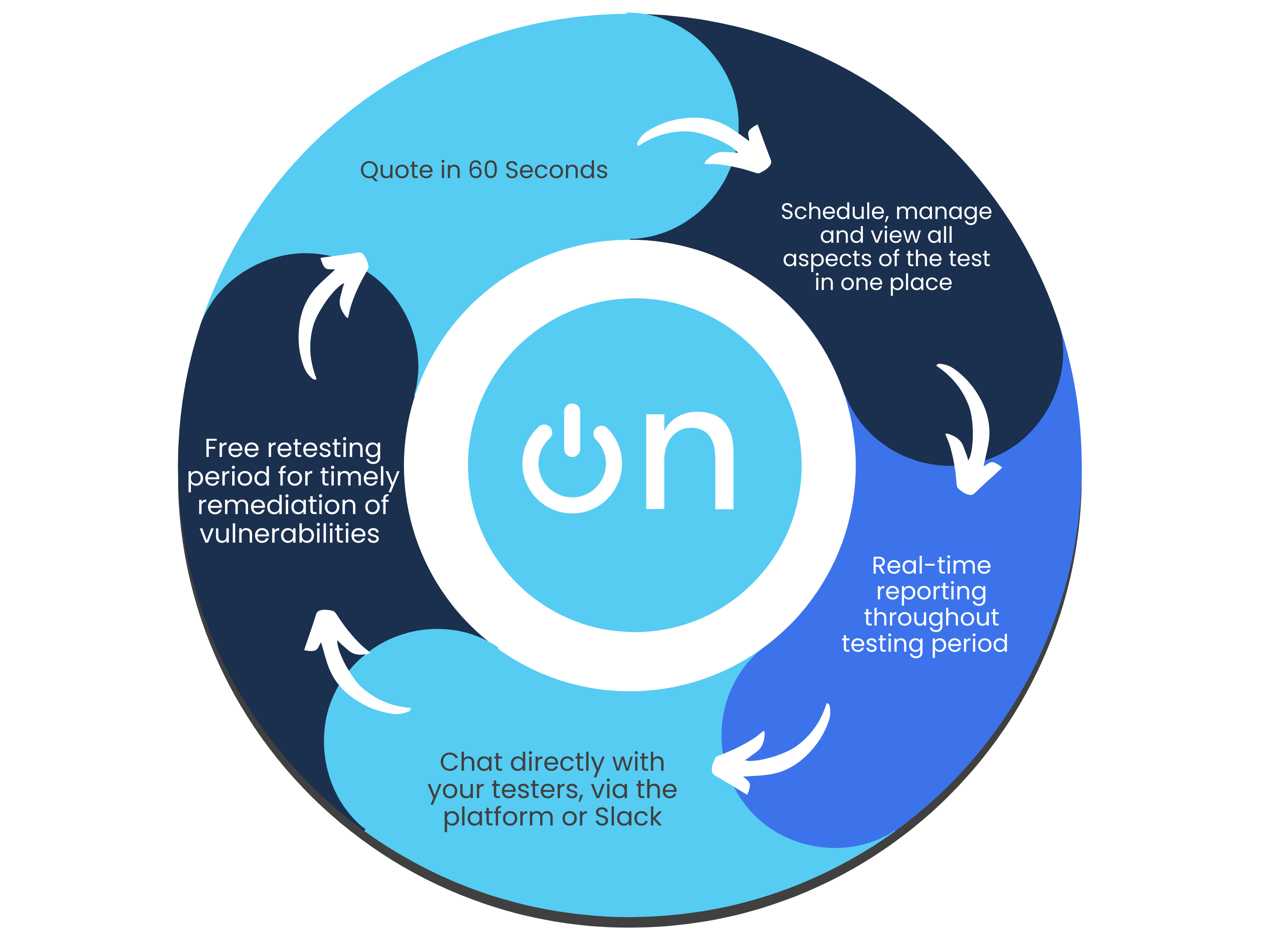
Simplify your testing and monitoring with a single monthly payment, combining regular penetration tests and continuous vulnerability scanning. Get predictable costs while receiving ongoing protection.Instant quote & customised plans
Receive a real-time, personalised cost estimate through our intuitive platform. Tailor your testing needs with configurable options that suit your business goals and security requirements.Effortless platform access
No more long scoping processes. Book tests directly through our platform or get personalised assistance from our sales team. Enjoy streamlined communication and automated workflow notifications for maximum efficiency.Continuous, real-time testing
Stay informed with real-time progress notifications and direct communication with testers via in-platform comments. Benefit from ongoing vulnerability assessments to proactively detect and address risks.Immediate, actionable reports
Access your findings instantly through our platform. Generate detailed reports at any time, offering both technical insights and high-level summaries—without the wait.Free retests for resolved issues
Once you’ve addressed vulnerabilities, we’ll retest them for free within a flexible window, ensuring your systems remain secure at no additional cost.Ongoing protection & threat intelligence
Sign up for continuous monitoring to access automated vulnerability scanning, along with situational awareness through threat intelligence, ensuring your defences stay up to date year-round.
Other types of penetration testing
Find the penetration test to best suit your business and cybersecurity needs.
Frequently Asked Questions
What devices do we cover during a mobile application penetration test?
OnSecurity will test both iOS and Android mobile apps. Whether written in Swift, JavaScript, or as a hybrid mobile application (using a language like ReactNative or Ionic), our team of experienced testers will be able to identify the technologies, interfaces, protocols and frameworks at use and customise the attack to suit your application.
How much does a mobile application penetration test cost?
Getting a quote for a mobile application pentest couldn’t be simpler - we don’t even need to speak to you! We just need the answers from two quick questions about your app, and we’ll provide you with an instant online quote, thanks to our testing team’s expertise. Our estimates are over 95% accurate.
Booking a pentest traditionally takes many emails and scoping questions back and forth. With OnSecurity you can get a quote and book in a pentest within 60 seconds - and we work in hours, not days. On average we are 38% more cost-effective than other vendors, thanks to precise hourly billing, no postponement or cancellation fees, and free retesting.
How often should you test your mobile application?
We recommend conducting mobile application penetration tests at least every six months or whenever significant new features are introduced, such as user management or payment functionalities.
When will I receive my pentest report?
Our testers provide real-time updates as they conduct their tests, so you receive immediate notifications when issues are discovered, rather than waiting until the entire test is complete and a report is generated.
How long does a mobile application pentest take?
The duration of a mobile application penetration test largely depends on the scope of the assessment, as well as the complexity and nature of the mobile app being tested. Depending on these factors, the testing process can range from a few days to several weeks.
Will my mobile application be disrupted during the test?
Our mobile app penetration tests are conducted safely and systematically by skilled professionals, making sure that there is minimal disruption to your operations. We provide real-time updates on any security vulnerabilities we discover, allowing you to address them quickly before they can be exploited by cybercriminals.
Will you help me in addressing the vulnerabilities identified during the penetration test?
Our team of mobile application testers knows both how to build and how to break applications. We will provide tailored remediation guidance for each vulnerability we identify. If you face any constraints, we’ll collaborate with you to understand them and suggest suitable solutions for each issue.
Can mobile application security testing be automated?
To some extent, yes. Automated tools can detect common vulnerabilities in mobile apps, but they cannot fully replace the detailed insights and nuanced analysis offered by manual penetration testing.
