Social engineering has become a top security threat. Safeguard your business with our social engineering assessments that identify the human vulnerabilities within your business by simulating real-world attacks to reveal where employees are most at risk. Gain immediate insights to strengthen security awareness, prevent manipulation, and protect sensitive information before an attacker exploits it.
Social engineering penetration testing
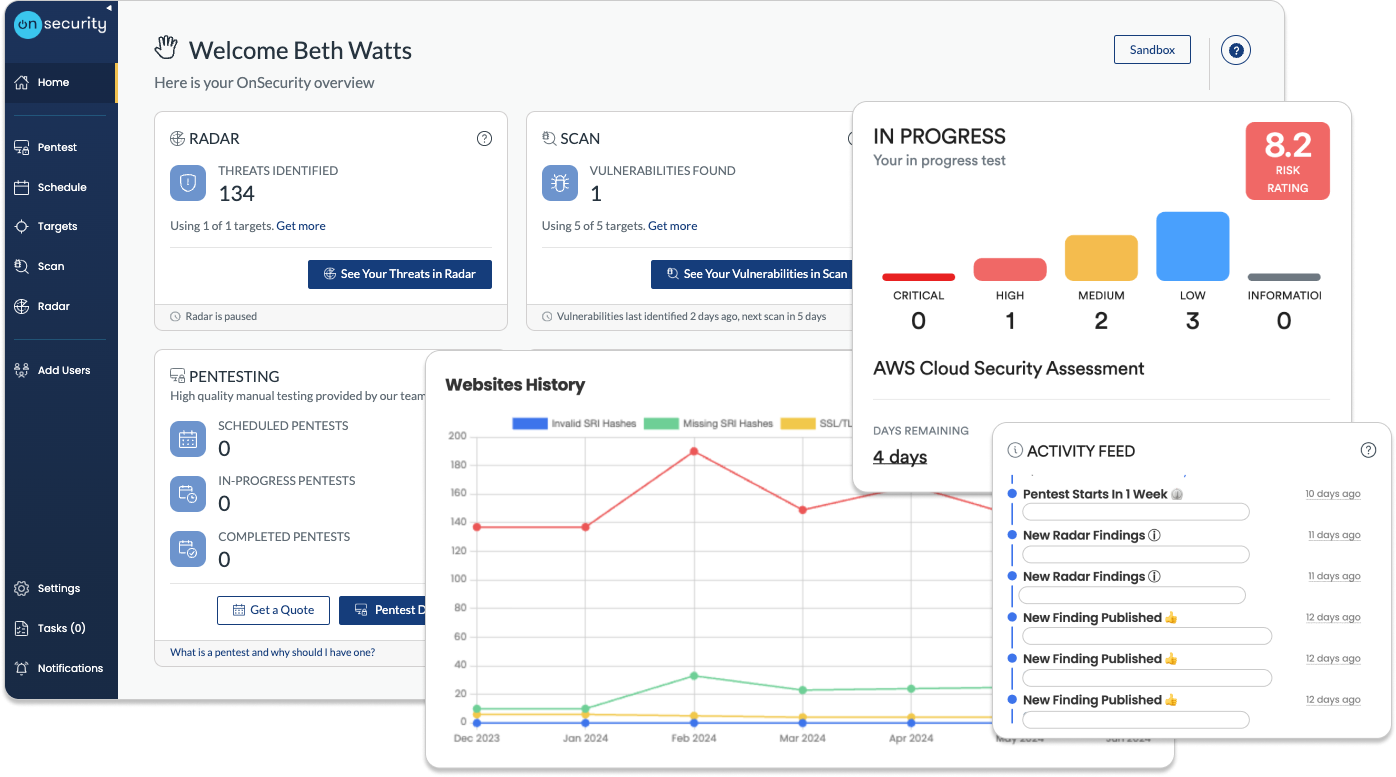
Social engineering penetration testing with OnSecurity
At OnSecurity, our social engineering assessments go beyond surface-level evaluations, providing expert-driven insights into the susceptibility of your employees to manipulation tactics.
Identify human vulnerabilities
You'll be able to reveal weaknesses in your organisation’s human defences that attackers could exploit, pinpoint employees most at risk of manipulation or deception and uncover gaps in staff awareness that could compromise security.
Mitigate data breach risks
Reduce the chance of attackers accessing sensitive data or systems, prevent unauthorised disclosure of confidential information and protect your organisation from reputational and financial harm.
Strengthen security posture
Gain insights into your organisation's resilience to social engineering attacks, improve processes to minimise exposure to social engineering threats and prepare your team to respond quickly to real-world social engineering attempts.
What is social engineering penetration testing?
Social engineering is a simulated attack designed to test the security awareness of your staff by exploiting human vulnerabilities rather than technical ones. This can be carried out over the phone, email, through your help desk, or via your web chat solution. The goal is to see if attackers could gain access to valid customer accounts or manipulate employees into revealing sensitive information.
Our testers thoroughly assess the potential attack surface for social engineering, conducting detailed research into your business, employees, and customers before launching a simulated attack. This process helps identify weaknesses and provides valuable insights to strengthen your company's defences against real-world social engineering threats.
Get a Social Engineering Pentest Quote
Want to know how much an social engineering pentest would cost? Try out our instant quote generator to get started.
Why do you need a social engineering pentest?
Your staff are the first line of defence against attackers, but it’s becoming increasingly common for attackers to simply call a company and manipulate an employee into granting access to a customer or staff account, or even other critical systems. This technique, known as social engineering, is rapidly growing as a preferred method for cybercriminals.
Just like traditional security assessments, social engineering tests provide a safe way to identify potential weaknesses in your security posture and address them before real attackers can exploit them.
Evaluate your staff's awareness of potential threats and uncover any gaps in your processes that could make your organisation vulnerable to a social engineering attack.


Crest-accredited social engineering pentesting
At OnSecurity, we offer top-tier social engineering penetration testing services, backed by our CREST (Council of Registered Ethical Security Testers) certification. This certification ensures that our testing methodologies, procedures, and standards adhere to the highest industry standards.
Why choose OnSecurity for your social engineering penetration testing?
- CREST-certified: Our services are externally validated, guaranteeing comprehensive and reliable testing.
- Experienced professionals: Our team is made up of CREST-certified experts skilled in conducting thorough social engineering assessments.
- Manual testing focus: We emphasise manual testing to identify vulnerabilities that automated tools may miss.
Rely on OnSecurity for expert-led, in-depth protection against social engineering threats.
Social engineering security challenges
Addressing social engineering threats involves understanding the unique risks associated with human behaviour and manipulation:
Human vulnerabilities
Employees can be targeted through deception and psychological manipulation, potentially compromising security.
Varied attack methods
Attackers may use diverse techniques, such as phishing, pretexting, or baiting, to exploit human weaknesses.
Ongoing tactics
Social engineering methods continuously evolve, making it essential to stay updated with current threats and employee training.
Quick, high-quality pentests
Discover why our user-friendly platform and AI + human approach make pentesting hassle- free.
Flexible subscription plans
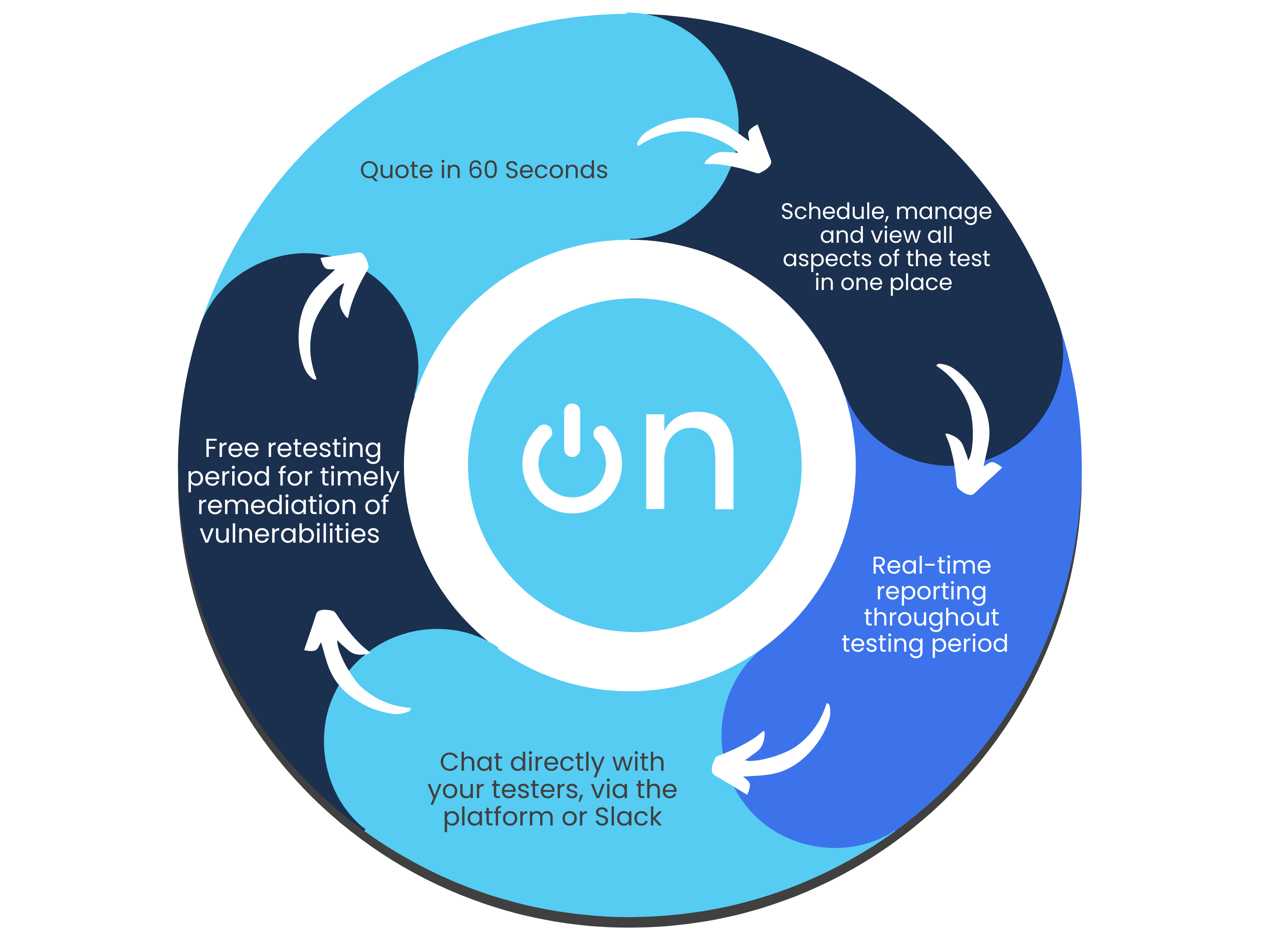
Simplify your testing and monitoring with a single monthly payment, combining regular penetration tests and continuous vulnerability scanning. Get predictable costs while receiving ongoing protection.Instant quote & customised plans
Receive a real-time, personalised cost estimate through our intuitive platform. Tailor your testing needs with configurable options that suit your business goals and security requirements.Effortless platform access
No more long scoping processes. Book tests directly through our platform or get personalised assistance from our sales team. Enjoy streamlined communication and automated workflow notifications for maximum efficiency.Continuous, real-time testing
Stay informed with real-time progress notifications and direct communication with testers via in-platform comments. Benefit from ongoing vulnerability assessments to proactively detect and address risks.Immediate, actionable reports
Access your findings instantly through our platform. Generate detailed reports at any time, offering both technical insights and high-level summaries—without the wait.Free retests for resolved issues
Once you’ve addressed vulnerabilities, we’ll retest them for free within a flexible window, ensuring your systems remain secure at no additional cost.Ongoing protection & threat intelligence
Sign up for continuous monitoring to access automated vulnerability scanning, along with situational awareness through threat intelligence, ensuring your defences stay up to date year-round.
Other types of penetration testing
Find the penetration test to best suit your business and cybersecurity needs.
Frequently Asked Questions
How long does a social engineering pen test take?
The duration of a social engineering penetration test can vary based on several factors. To provide a tailored estimate, we need to answer just two simple scoping questions. This helps us assess the complexity of your environment, as well as the size and scope of your targets, allowing us to give you a more accurate timeframe for the test.
How often should you conduct a social engineering pentest?
It's recommended to run social engineering penetration tests regularly to stay ahead of evolving threats. Aim for an annual test to keep up with new tactics. Also, test after major changes to your systems, policies, or team structure, and following any security incidents or attempts. Regular testing helps ensure your defences are always sharp and ready to handle potential social engineering attacks.
When will I receive my pentest report?
Our testers provide ongoing updates throughout the testing process, notifying you directly as vulnerabilities are discovered. This keeps you informed of any issues in real time, allowing you to address them immediately rather than waiting for the final report.
Will my systems be disrupted during the test?
Our skilled professionals conduct social engineering penetration tests with great care to avoid significant disruption to your operations. To minimise impact, we can carry out tests in UAT, staging, or development environments. We also provide ongoing updates throughout the testing process, so you can promptly address any security concerns as they arise.
What will we find in a social engineering penetration test?
A social engineering penetration test will uncover various vulnerabilities related to human factors and security awareness. You’ll identify how susceptible your employees are to manipulation tactics such as phishing, pretexting, or baiting. The test will also reveal weaknesses in your current security practices and training programmes, highlighting areas for improvement. Additionally, you’ll gain insights into the effectiveness of your existing safeguards and pinpoint specific areas where attackers might exploit human factors to gain unauthorised access.
Is social engineering testing right for your business?
Social engineering testing is right for your business if you want to evaluate the effectiveness of your employees’ responses to manipulation tactics and identify potential vulnerabilities in your human security defences. This type of testing is particularly valuable if you handle sensitive information or operate in an environment where human error could lead to significant security breaches. By simulating real-world social engineering attacks, you can uncover weaknesses in your staff’s awareness and training, allowing you to strengthen your overall security posture and reduce the risk of costly security incidents.
What are examples of a social engineering test?
Social engineering tests assess how well employees handle deceptive tactics such as phishing, vishing, and smishing. Phishing emails attempt to trick individuals into revealing sensitive information or clicking malicious links, while vishing involves attackers making phone calls and posing as trusted sources to obtain confidential data. Smishing, on the other hand, uses text messages to lure people into sharing personal details or downloading malware. These tests are typically conducted off-site, though on-site assessments can also be used to simulate real-world scenarios. By simulating these threats, we evaluate your team’s ability to recognise and respond effectively, enhancing your overall security awareness and resilience.
What is the difference between our social engineering penetration testing and phishing pen testing?
Social engineering penetration testing includes various deceptive tactics, such as phishing, vishing, and smishing, to evaluate how employees handle different manipulative strategies. Phishing pen testing specifically targets email-based attacks where individuals are deceived into disclosing sensitive information or clicking harmful links. While phishing is a key part of social engineering tests, the latter covers a wider range of methods. For more details on how our services can align with your needs, please contact us so that you can receive the most relevant testing for your business.
Alongside penetration testing, we also advise continuous vulnerability scanning, and threat intelligence. Staying proactive with patch management and remediation is essential. If you have more questions to help select a reputable pen testing service, don’t hesitate to get in touch.
