What does my business need to be cyber secure?
Recent reports from Cybersecurity Ventures suggest that the global cost of cybercrime will grow by 15% year on year until it reaches $10.5 trillion dollars by 2025.
To reduce risk in this increasingly hostile environment, the approach we take to cybersecurity must continuously evolve above and beyond foundational practices. However, it is still important to frequently check the basics.
Cybersecurity doesn't have to be overwhelming for business owners. By being aware of the following topics, you can save time, money, and protect the reputation of your business. While no blog can guarantee complete protection against all cyber threats, these steps can mitigate the chances of your business falling victim to cybercrime.
Passwords
Implement a strong password policy. We advocate for a greater reliance on technical defences and organisational processes. Passwords should make up just one part of your wider access control and identity management approach. That being said, it’s still important to maintain good password hygiene and complexity standards.
Anti Virus/Malware
Use anti-virus and anti-malware software: Make sure all devices and systems are protected from viruses, malware, and other malicious software. The cost and disruption of a ransomware attack to a business can be crippling.
Software Patching
Keep software and systems up to date: Regularly update all software and systems to ensure they are protected against known vulnerabilities and the latest bugs. Keeping everything running smoothly is mission critical, and a lapse in patching could be critical for an organisation.
Firewalls
Firewalls can improve business resilience and provide controlled access to company resources. We recommend utilising a firewall to safeguard your Internet connection. This establishes a protective barrier, commonly referred to as a "buffer zone," between your internal network and external networks. In its most basic application, this barrier is established between your devices and the internet. By inspecting incoming traffic within this zone, you can effectively determine if it should be granted access to your network.
Encryption
Use encryption everywhere. Encrypt all sensitive data, both in transit and at rest, to protect it from unauthorised access or during a data breach. As simple as it may sound, time and time again we are seeing data breaches where the data has not been encrypted.
Training
Train employees on cybersecurity best practices: Regularly educate employees on how to identify and avoid phishing scams, suspicious emails, and other security threats. By making our employees aware of what they need to look out for, it can greatly reduce the chance of a successful phishing campaign.
OnSecurity can help you test your organisation's susceptibility to phishing attacks and help improve your employee's awareness of phishing scams. Prevent phishing attacks with OnSecurity now with: Phish By OnSecurity.

MFA
Use multi-factor authentication: Implement multi-factor authentication for all accounts and systems to provide an additional layer of security.
Security keys can be a big bonus here. You can read more about that in our blog here.
Backup data
It’s critical that backing up data is a key part of any cybersecurity strategy. There is an extremely good availability of plug and play backup solutions available to take advantage of, and the majority offer automated backups, which can reduce human error and increase security of your data. When choosing a solution, it’s important to consider how much data will be backed up, and how quickly you may need to access that data following an incident, with mileage varying from provider to provider.

Incident Response
Have an incident response plan. Have a plan in place to respond to and recover from a security incident. According to the National Institute of Standards and Technology (NIST), there are four phases to most effective incident response plans:
Preparation Detection and analysis Containment, eradication, and recovery Post-incident activity.
Cyber incident response is critical to all organisations. It also covers the report producing stage of a potential breach, which describes the scope of the problem, the technical impact, and how it is affecting the core organisation and its partners, while providing mitigations and further recommendations.
Incident response plans make up another crucial part of an organisation's overall cybersecurity strategy, so it’s important to be aware of it, and understand how it can benefit your business.
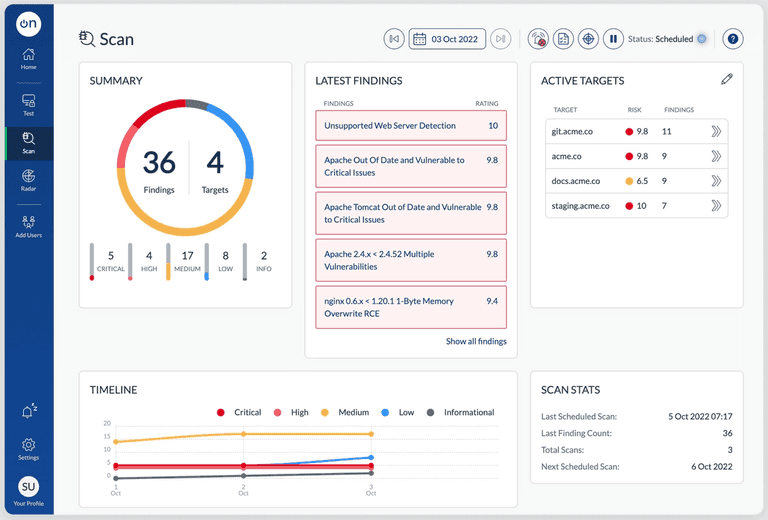
Vulnerability scanning
Vulnerability scanning is an important aspect of a comprehensive security strategy for businesses. It helps organisations identify and assess potential vulnerabilities in their IT systems, networks and applications. This can include known vulnerabilities, misconfigurations, and missing patches.
With the increasing number of cyber attacks and the complexity of modern IT systems, many regulatory compliance standards, such as PCI-DSS, HIPAA, and NIST, require regular vulnerability scanning as part of their compliance requirements.
OnSecurity understands the importance of safeguarding your online presence and that's why we offer a range of comprehensive cybersecurity solutions that will help your organisation stay safe.
Scan by OnSecurity offers continuous external vulnerability scanning and management of your Internet-facing assets. Stay ahead of the threats and start scanning your assets for vulnerabilities today, follow the link here: Scan By OnSecurity.
Penetration Testing
The National Cyber Security Centre (NCSC) defines a penetration test as a “method for gaining assurance in the security of an IT system by attempting to breach some or all of that system's security, using the same tools and techniques as an adversary might."
Penetration Testing can be one of the most effective ways to protect your assets and data, and is a critical function of any cyber security strategy. However, A penetration test can only validate that your organisation's IT systems are not vulnerable to known issues on the day of the test. This is why it’s important to have frequent and effective penetration testing against all company assets.
A well-scoped pentest provides the consumer confidence that the products and security controls tested have been configured in accordance with best practices and that there are no common or publicly known vulnerabilities in the tested components.
Schedule your pentest with OnSecurity OnSecurity is a CREST-approved vendor, and all our testers are qualified CREST testers. OnSecurity offers a wide range of industry leading penetration testing services to clients all over the world.
What are you waiting for? Get an instant quote now!





