What is ISO 27001 certification
ISO 27001 outlines the gold standard for information security management systems (ISMS).
The ISO 27001 framework helps organisations of any size and from any vertical set-up, maintain and build on their ISMS. Adopting a gold standard ISMS supports organisations in preventing cyber attacks and security incidents, and ensures they stay compliant with changing regulations.
To comply with certification, organisations must build a suite of security controls to identify and address security risks across their networks and ensure they are meeting changing security needs over time.
Why is ISO 27001 certification important?
ISO 27001 is a voluntary standard. However, we recommended that businesses follow and comply with legal requirements as attaining certification offers many benefits.
Amongst helping organisations become risk-aware and proactively identify and overcome weaknesses, certification shows customers your commitment to secure information management and emphasises your business's trustworthiness towards customers, which, in turn, helps organisations secure new business.
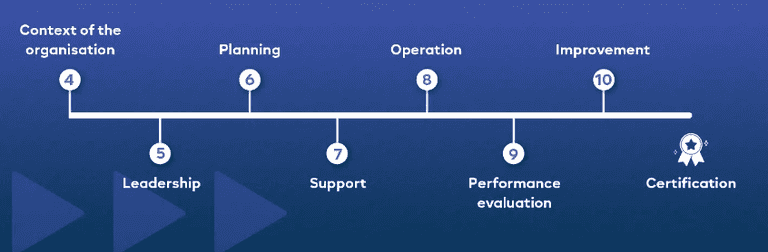
ISO 27001 checklist
There are many moving parts to achieving certification which can become overwhelming for even the most experienced security teams. Therefore, we hope using this ISO 27001 checklist will support and direct security professionals to prepare and implement each component correctly.
ISO27001: Easy-to-follow guide
Step 1: Gap analysis
To maintain simplicity throughout this process, you should first conduct a gap analysis. Businesses should compare their current ISMS against the requirements for ISO 27001 and identify gaps in their security infrastructure.
By completing this at the very beginning of the process, businesses can define and plan how they are going to prioritise vulnerabilities and track the necessary required steps in order to revamp business standards. This will provide businesses with a clear roadmap and actionable steps to improve practices.
Step 2: Identify areas requiring protection
For those companies seeking certification for the first time, they will need to identify the parts of the ISMS that require protection. An ISMS consists of technology, processes and people so it is required for businesses to look at how information is accessed, who has access to it and when is it accessed.
Based on the information above, it is important for security teams to limit the access of this data to only certain individuals within the security department to prevent a data breach. Businesses should document each touchpoint for the data points and set policies to protect it throughout its lifecycle.
As an additional layer of protection, businesses should run regular penetration tests to ensure their applications are secure from attacks. OnSecurity offers penetration testing with real-time reporting and on-demand scheduling, providing hundreds of businesses with the operational threat intelligence they need to improve their security status and achieve certification.
A penetration test provides evidence to the auditor that the organisation is taking proactive measures to secure all web application vulnerabilities and prevent attacks.
Book your penetration test today!
Step 3: Risk assessment
By now businesses should have a clear understanding of their raw data, how it is used, how it is managed and the risks associated with it.
To complete an internal business risk assessment they should be asking themselves, how likely is it that these types of attacks will occur and if they did, what would be the overall impact? We recommend using a risk matrix to proactively assess potential attack methods and associated risks, enabling them to prepare and overcome any business threats as smoothly as possible.
Remember, ISO 27001 relies on clear documentation, so businesses should make note of every step taken to improve the intelligence cycle. This will come in handy during the audit process.
Step 4: Start making some changes
After comparing the policies and controls against the ISO 27001 requirements, it's time to update the workplace's systems.
Data handling procedures, policies, and software may need to be updated to meet the requirements of the improvements. For example, if you have stated that your business will use vulnerability scanning to detect vulnerabilities in your internet-facing infrastructure and to improve raw data management, you will need to implement that into your strategy.
OnSecurity offers 24/7 vulnerability management. With this tool, businesses can find and fix vulnerabilities before an attacker does. Implementing this into a business's security strategy to manage technical vulnerabilities will improve the chances of achieving certification.
Try OnSecurity's vulnerability management tool today
In addition to utilising tools, the appointed security team should receive appropriate security awareness, education and training to understand the business's security posture, which will support them to manage risk and prevent potential threats.
Step 5: Put your changes to practice
At this point, businesses should have everything in place to pass an audit. However, we recommend conducting an internal audit to prepare themselves for the real thing. This way organisations can identify if their tools are working and provide them with the opportunity to improve intelligence requirements before the official audit.
Once they are suitably prepared, businesses should invite an accredited ISO27001 auditor to complete a two-stage audit. Firstly, they will access your documentation and the controls put in place to improve the attack surface and combat cyber threats. Secondly, they will conduct a site visit to establish if your business has an ISMS that complies with ISO 27001. They will also be reviewing evidence that the organisation is visibly following the documentation that was reviewed in stage one of the audit and accessing the incident response measures
If the auditor is satisfied with what they find, they will issue businesses with an ISO 27001 accreditation which will last three years. Ongoing risk assessments and surveillance audits should be complete throughout the time to ensure you're prepared for renewal in the third year.
How can OnSecurity help with your ISO 27001 certification?
Operational threat intelligence, vulnerability management and penetration testing
OnSecurity offers operational threat intelligence, vulnerability management and pentesting services to prevent emerging cyber threats for over 300 customers worldwide. We oversee and review entry to your databases, servers, clusters, and web applications, reviewing and documenting all the touch points found in your risk assessment. With this information you can evaluate the necessary controls and implementation required for optimal efficiency.
Using OnSecurity to support your compliance journey goes above and beyond ticking the box for ISO 27001, we ensure customers have a clear understanding of their security posture at a point in time and provide support to identify and treat root causes, not just the symptoms.




