What is threat intelligence?
Threat intelligence involves gathering, analysing, and applying information about potential or current cyber attacks that could threaten an organisation's security. It provides insights into threat actors, their tactics, techniques, and procedures, as well as indicators of compromise.
The ultimate goal of threat intelligence is to equip organisations with the knowledge to proactively defend against and respond to cyber security threats. It can help you take action to limit the impact of an attack before the attack even takes place.
Why do I need a cyber threat intelligence tool?
A cyber security Threat Intelligence tool is vital for proactively identifying and combating potential threats. It provides real-time insights into emerging risks, enabling swift and effective incident response. It aids in threat prioritisation, ensuring efficient resource allocation.
This tool also enhances risk management by offering a clearer understanding of your organisation's security posture. By keeping you informed about the latest cyber threats and trends, it contributes to building a robust and resilient cyber security strategy.
Threat intelligence and understanding your exposure level is key to transitioning from reactive to proactive cyber security and can further support your security teams strategy.
Check out our threat intelligence tool free for 14 days now
How does threat intelligence work to combat cyber threats?
Threat intelligence tools work by collecting data about cyber threats from various sources, including the open web, dark web, and internal systems. Data is then analysed by firstly, mapping your internet facing infrastructure and searching the web for issues related to assets you own. These are then organised into actionable intelligence about potential or current attacks, threat actors, their methods, and associated vulnerabilities.
These tools facilitate real-time alerts on identified threats, enabling organisations to respond promptly and effectively. They also help in prioritising threats based on their potential impact, improving incident response and risk management strategies, enabling businesses to act before data breaches and possible reputational damage.
Threat intelligence is also required to secure ISO certifications which further enhance businesses' legitimacy and reputation.
Using threat intelligence solutions to achieve ISO 27001 certification
ISO 27001 outlines the gold standard for information security management systems (ISMS). Using the ISO framework, organisations are guided on the best-practice approach to securing sensitive information, data sources and security systems by using processes, technology and people. The latest 2022 Standard requires businesses to use threat intelligence to collect and analyse data in order to achieve this certification.
An ISMS enables organisations to better prevent cyber attacks and other security incidents, as well as keep up with evolving regulatory requirements.
As part of ISO certification, organisations are required to demonstrate compliance with specific security standards, as well as conduct regular audits to assess the impact of security tools. By proactively collecting and analysing intelligence reports, threat intelligence tools support compliance by providing ongoing security analysts and evidencing the comprehensive measures taken to prevent future cyber threats.
Threat intelligence enables incident response teams to make informed security decisions and react in real time to combat any known security vulnerabilities. By having tight vulnerability management and operational threat intelligence tools in place, businesses are likely to secure their ISO certification.
Start your compliance journey with OnSecurity today!
What makes our threat intelligence tool different from the others?
Radar has the ability to pull threat data from multiple sources. By processing over 14 billion breached credentials, motoring over 20,000 sites and over two million domains a year, this threat intelligence tool is able to present an accurate view of an organisation's threat level.
Scanning information from across the internet and dark web, OnSecurity's threat intelligence tool scopes out how exposed your organisation is to potential threats and provides concurrent threat data to map your attack surface, alerting you to any threats against your IP addresses, domains, passwords and other exposed credentials.
Radar is a simple-to-use tactical threat intelligence solution suitable for organisations who may or may not have a security team and is appropriate for those companies without a big enterprise budget. It can guarantee a good level of assurance for businesses without requiring constant monitoring and security knowledge, and will protect all types of businesses from common attack vectors.
Our threat intelligence platform helps you prevent future attacks by focusing on four key areas: domain threats, password threats, website threats and ongoing attack surface monitoring.
You can start your free 14-day trial here
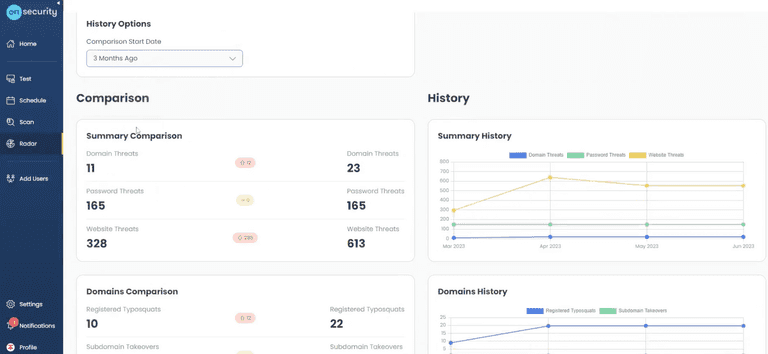
Now, let's look a little deeper into how monitoring those four areas can improve organisational threat intelligence.
Domain Threats
A domain threat is a risk or vulnerability that can compromise the integrity and security of a domain, including a website, network or online presence. There are many potential risks associated with these threats, including data breaches, unauthorised access, financial loss, and reputation damage.
Radar constantly scans against domain threats to identify any malicious actors and false positives. The common threats include:
Registered Typosquats
An attempt to collect data and acquire sensitive information by registering a similar domain and targeting people with malicious file hashes and malware links. Radar will list similar domains within the portal and alert clients of any that could indicate a cyber attack in progress.
Subdomain Takeovers
An extremely common and high-severity vulnerability that can occur when you have subdomains that point to open DNS records. Radar detects any instances of vulnerable subdomains and notifies businesses of these threat indicators.
Certificate Monitoring
Every time a new TLS certificate is issued, an entry is created for it in a global, public log known as the Certificate Transparency Log. Analysis of this log in real-time can provide a number of powerful security capabilities, and Radar does exactly that.
The Certificate Monitoring module will monitor the Certificate Transparency Log for any registrations that contain your company's name, domain name or other significant words to your organisation.
Most modern phishing attacks will have to employ a TLS certificate, otherwise, often the browser won’t load the phishing site, or at least give a warning to the user. So, by monitoring the Certificate Transparency Log, you can see if anyone’s registering fake domains to use against you in a phishing attack, for fraud or impersonation.
Radar’s certificate monitoring can also be used to monitor for unauthorised certificates that are created by staff members within your organisation, giving you an out-of-the-box shadow IT monitoring capability.
Password Threats
Password attacks are one of the most prominent security concerns and responsible for the most data breaches worldwide. In 2022, Cybercrime Analytics (C2A) provider SpyCloud, discovered 721.5 million exposed credentials online. Therefore, it is with utmost importance to deploy high level security processes to passwords across businesses to prevent attacks.
There are different types of password threats:
- Breached Credentials
Lists of breached credential combinations are commonly found when a large organisation has been hacked. The attackers will leave or sell sourced credentials on the web, where other bad actors will use them across other services via brute forcing.
- Reusing Credentials
Reusing credentials is another common mistake. People will fall victim to an attack when they use the same email and password combination across multiple sites. This form of attack is known as credential stuffing. According to the Annual Identity Exposure Report for 2022, 64% of people reuse the same password on multiple accounts. This leaves personal or business raw data in a dangerous position.
By comparing passwords found across multiple breaches, Radar can determine if one or more of your staff are reusing the same password across multiple sites. This is very dangerous behaviour, as a compromise of the password in one breach means an attacker could trivially access other accounts for that user.
Radar also analyses the strength of any breached passwords, providing another very useful indicator of password hygiene in your organisation.
Website Threats
Website threats can appear when common browser security features such as sub-resource integrity hashing or security headers are missing or invalid, presenting an opportunity for an attacker to launch their own malicious code.
It’s important to have visibility into the technologies and third party scripts used across your websites, as anything in your supply chain could present a risk to you if compromised. Radar provides full visibility into website vulnerabilities and will scope any potential threats.
Is it worth investing in a threat intelligence platform?
Threat intelligence platforms offer a unique insight into intelligence data that puts you a step ahead of any cyber threat and cyber attacks.
Having a threat intelligence solution provides real-time visibility into the vast digital landscape and empowers clients to take proactive action to disrupt multiple threat feeds. The intelligence tool makes it easier for businesses to share external threat information across both technical and non-technical stakeholders.
Clients will want to see a business with a secure and trustworthy strategic threat intelligence programme before investing heavily into products or services.
In a nutshell, Radar has its own portal that displays all the necessary information about an organisation's attack surface i.e. its external infrastructure.
The platform includes mapping of your attack surface and monitoring of changes to domains, subdomains, DNS records, web servers, IP addresses, and open TCP ports.
Radar is designed to give you the situational awareness to protect your business from common cyber attacks. This tool evaluates overall threat level and rapidly triages your risks and builds custom security workflows in your existing tools, via enterprise integrations.
Radar is constantly iterating to provide customers with the assurance that they are protected against the common vulnerabilities often utilised to target organisations for compromise.
Are you thinking about investing in threat intelligence? We offer free threat intelligence with our 14-day free trial.




