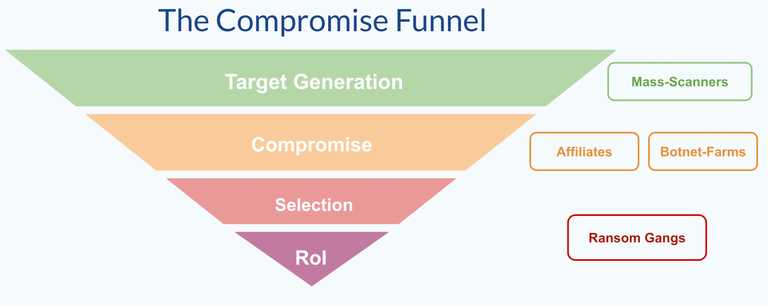
This image is what we at OnSecurity call the 'Compromise Funnel'. It serves two purposes.
-
It maps out how modern cyber-crime organisations work (and work together).
-
It provides a realistic starting point for thinking about how to defend your business.
I'll talk about point 2 in a later post, for now let's focus on point 1.
How does this actually work?
The compromise funnel conceptualises the path your business follows while moving from "everything is rosy in the garden" to "our customer database is on pastebin".
A compromise of a business doesn’t just “happen”.
They roughly follow the steps outlined in the compromise funnel, and it's common for completely different crime organisations to operate in different parts of the funnel.
Let's walk through the steps.
1. Target Generation
This is the 'lead generation' of the cyber-crime business, and involves rapid, continuous, large-scale, mass-scanning of the internet; hunting for any businesses that have weaknesses.
These weaknesses can either be avenues of direct compromises, or (more commonly) merely be indications that the business is not following security best practices. Weak or vulnerable targets are passed down the funnel for Compromise.
2. Compromise
The most difficult step in the funnel - actually compromising the target. The investment from the cyber-criminal organisation here can be significant, with 'loitering time' sometimes being multiple months.
3. Target Selection
Not all businesses are created equal. Target selection will take the pool of compromised businesses and select the highest potential value targets for compromise.
This can be very sophisticated and uses similar techniques as the B2B sales industry does for lead selection.
Factors such as potential payout, ease of compromise, type of organisation etc all come into play here (an example here is that Revil won’t go after anyone with less than $4m annual turnover).
4. Return on Investment
Cyber-crime is a business and needs to make a profit. This might take the form of Ransomware payment, sale of leaked info, extortion, bribery, etc etc. In most cases there needs to be a pay-off for an attacker.
It’s important to note that different organisations operate at different layers of the compromise funnel. For instance, bot-farms and affiliate networks operate at layers 1 & 2, while RansomWare gangs like Revil and Babuk operate at layer 3 & 4 typically.
Organisations at each layer specialise in certain tasks, and sell their output down to the next layer.
The eagle-eyed among you probably recognise that the compromise funnel is very similar to a typical B2B sales funnel, which it is. The sales and cyber-crime industry are very similar (except the sales industry has more criminals, hyuk hyuk).
So, what lessons to take out of this?
Well, lots, but rule number 1 is that you NEED to know if you're in the compromise funnel. Because the bad guys sure as hell do.
That’s why OnSecurity created our threat and attack awareness tool, Radar. You can’t always avoid entering the compromise funnel, as there’s too many factors that could put you on an attacker’s radar (no pun intended).
The important thing is to be aware of any potential attack vectors, so you can act to prevent your organisation being successfully compromised, and passed down the funnel.
Want to see what Radar can see about your organisation? You can try it for free here.




